In this article, I'll show you how to deploy the lambda that we constructed in the previous section. This time, we need to set up AWS in preparation for deployment.
If you missed Part 1, please read it first.

No costs!
To test deployments, there is no cost; Amazon has a free tier for lambdas, so you can deploy as many lambdas as you want; you will pay once you exceed the following limits:
- 1 million free requests per month
- 3.2 million seconds of compute time per month
⚡ So be careful to write any lambdas that involve image or video processing, or that run for a long duration of time, because you'll most likely pay for it, and keep in mind that there is a 900-second execution limit (15 minutes).

Requirements
- Please create your AWS account to test deployment.
AWS Access Key
After you've created your account, you'll need to create a user and set your AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEYPerhaps you are receiving a privilege-related problem; check to see if you have missed any policies for your user., and AWS_DEFAULT_REGION environment variables.
You can set these values in your profile (.bashrc, .zshrc, .profile, or bash_profile).
Group and privileges
Now we need to assign some privileges to your user, who will be in charge of deploying AWS Lambda through Serverless, Create a group, attach it to your created user, and provide the following permissions:
- AmazonAPIGatewayAdministrator
- AWSCloudFormationFullAccess
- AWSCodeDeployFullAccess
- AWSCodeDeployRoleForLambda
- AWSLambdaBasicExecutionRole
- AWSLambdaFullAccess
Role for AWS Lambda execution
If you did not specify an iam/role before deployment, Serverless will manage a user for you if the user has permission to create roles. In this example, I tried not to use this magic; in my opinion, allowing a tool to set your lambda permissions is not a good idea...

Then let's create some roles; we can ask Amazon help to create a Lambda-specific user, as I did below:
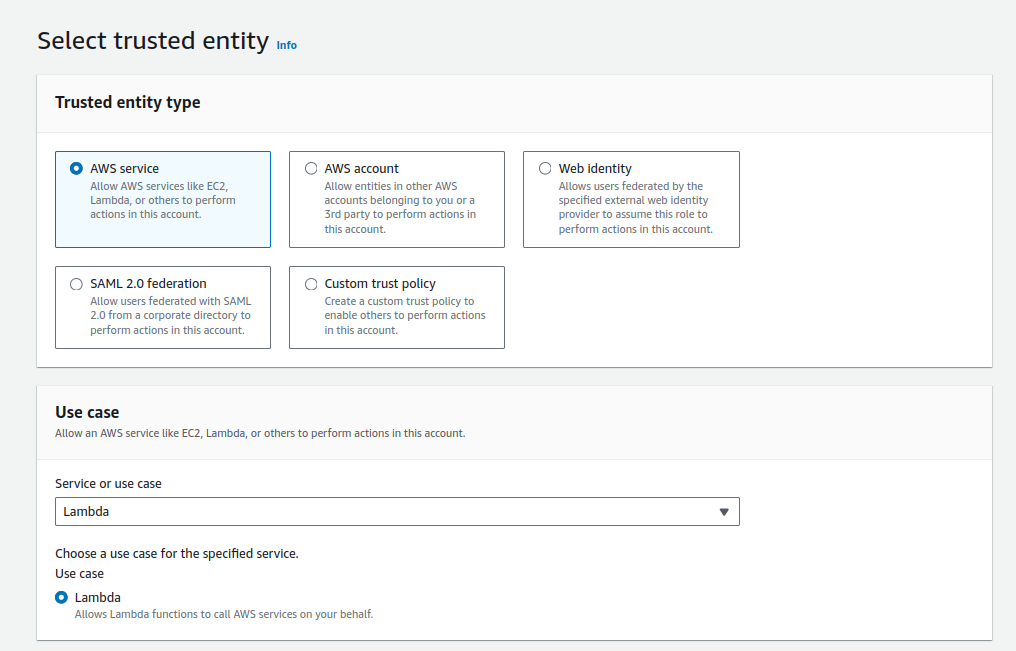
After we create this role, you must copy the ARN and specify it at deployment.
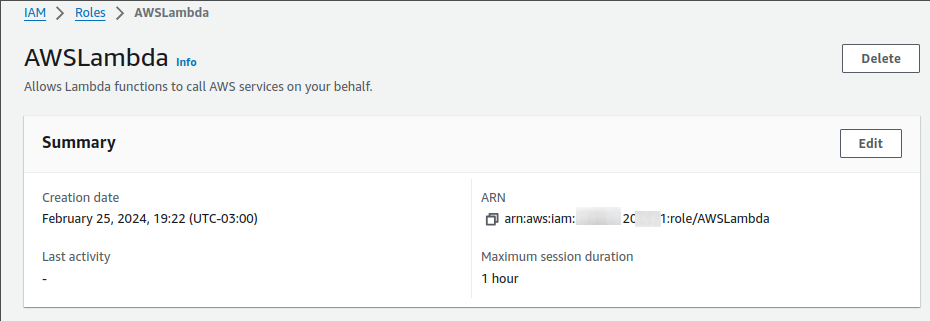
This is fantastic, however we construct a Lambda user who has access to any AWS resource, thus it's an excellent security question for production scenarios. I recommend that you create something specifically for your lambda. It's hard but safe.
The latest lines in the file refer to skipping node_modules during package deployment.
Deploy
If everything is set up correctly, the deployment will be successful. As an ordinary Friday deployment. 😜
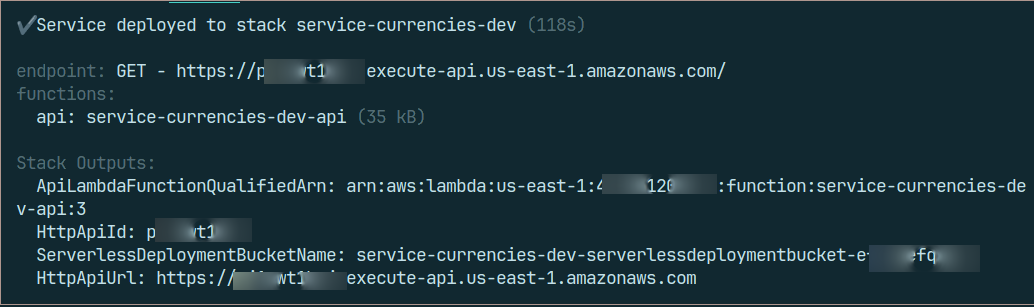
That's it; your public service has been deployed, and you may test the ApiUrl exposed after deployment.
Issues
- Perhaps you are receiving a privilege-related problem; check to see if you have missed any policies for your user.
- Remember to configure your AWS keys in your profile or via a shell session if you want.
Removing
To avoid spending money 💸 on a public test route, use the following command to remove your lambda function.
That's all
Thank you for your attention, I hope that my piece has helped you understand something about Lambda and has encouraged you to learn more about not only AWS but also Cloud.
Please keep your kernel 🧠 updated. God gives us blessings 🕊️.




